Along with control of US air space and outer space, the US Air Force is tasked with maintaining control of cyberspace. And our men and women in blue are calling on contractors to help them do some very heavy cyberlifting, as well as to provide an extended range of other, IT-related, services.
The vehicle for all this is the Department of the Air Force, Air Force Materiel Command, Air Force Life Cycle Management Center, Business and Enterprise Systems Directorate (AFLCMC/BESD) Small Business Enterprise Applications Solutions’ IDIQ (AF SBEAS) contract.
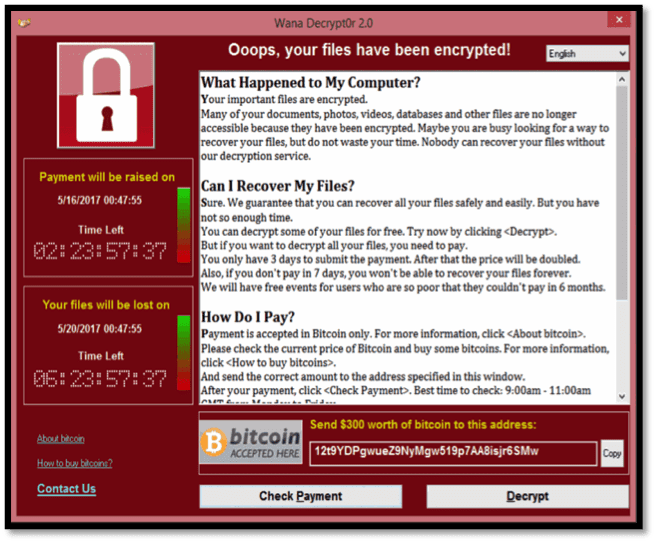
PAY UP! – Or access will be denied. The recent WannaCry malware attack may have been just the beginning.
SBEAS is a continuation of NETCENTS II, which twelve companies are presently working on — Datum Software, Diligent Consulting, Diversified Technical Services, DSD Labs, Digital Management, Exeter Government Services, Indrasoft, Segue Technologies, SI Systems Technologies, Array Information Technology, and Actionet. NETCENTS II is scheduled to end in June, 2019.
Its replacement, SBEAS, a draft of which hit the street last March 24, has an estimated value of….a whopping $13.6 B.
SBEAS is a Small Business Set Aside, 100%. Competition is expected to be fierce; over 200 individuals attended each of the two separate Industry Day/Site Visit presentations which were held November of 2016 and then last April. SBEAS winners will have their work cut out for them — as recent events have shown.
Locked Out

BITCOIN – This Crypto currency can be used to hide cybercriminals and their like.
On Friday, May 12, a barrage of cyberattacks rained down on computers in over 150 countries. So-called WannaCry ransomeware swept across Europe and Asia like a plague of cyber locusts, locking up critical IT systems.
When folks at the UK’s National Health Service and a large Spanish telecom and at various other businesses and institutions, worldwide, tried logging in, what came up on their computer screens, monitors, handhelds …. was a ransom demand for roughly $770,000, to be paid in the crypto currency, Bitcoin, or else their systems would be locked down…..indefinitely.
Typically, France’s auto manufacturer, Renault, was forced to idle some of its factories, only for a while though.
Lucked Out
Because, as luck would have it, a 22-year-old British computer geek/expert, Marcus Hutchins, also known as MalwareTech, quickly found a way to stop and work around WannaCry. Computer access was quickly restored. And it’s believed that these malicious perpetrators received a paltry $20,000 for all their trouble.
That said, MalwareTech has warned that another, similar, attack is likely soon, one that works around his fix. So, um, ah…next time….?
What Will Happen When the Luck Runs Out?
Incidents like the WannaCry attack keep our men and women in Air Force blue, and their contractors, awake at night. WannaCry (also called WannaCrypt, Wana Decryptor or WCry) was purportedly based on weaponized malware stolen from the National Security Agency (NSA) in April. The fact that someone found a way to wreak havoc on IT systems worldwide with American-developed cyberweaponry is worrisome to say the least. Could a way be found to attack the supposedly super secure mission-critical and sensitive IT platforms supporting the vast array of weaponry in America’s formidable and technically advanced arsenal? And are our military and civilian commo and analytical systems, systems vulnerable as well?
This is the sort of challenge winners of the SBEAS contract will have to contend with.
SBEAS Update
On May 22, a letter went out clarifying SBEAS Joint Venture Agreement (JVA) requirements. (The letter, and other solicitation material, can be found on the following site: https://www.fbo.gov/s=opportunity&mode=form&tab=core&id=9318b410d0bfd53d07ccf5a430fc7f6a ). They’re supposed to be addressed through a submission now due June 16. So, companies planning to bid better hurry up and send theirs in, pronto.
Multiple awards are expected. And — Price will not be an evaluation factor in this contract award. Repeat: PRICE will NOT be an evaluation factor in this contract award.
But – This is a one-to-a customer affair — strictly.
As AF officials have made very clear to potential SBEAS bidders:
“Only one proposal may be submitted by an offeror in response to this requirement. It is NOT permissible for the same company to submit multiple bids for this solicitation. In addition a company/offeror may not be a member of multiple JVs.”
Cybersecurity….and So Much More
Here is what’s specifically called for in the SBEAS proposal on the Cyber front: “… Experience integrating DoD and/or National Institute of Standards and Technology (NIST) Information Assurance/Cybersecurity concepts, practices, and procedures for an IS within the network environment.”
But the scope of this ID/IQ is larger than cyberwork. It includes the comprehensive suite of IT services and IT solutions to support IT systems and software development in a variety of environments and infrastructures. Also additional IT services including: documentation, operations, deployment, cybersecurity, configuration management, training, commercial off-the-shelf (COTS) product management and utilization, technology refresh, data and information services, information display services and business analysis for IT programs.

ROLL THE DICE? – Risk Minimization and Management will be key to winning SBEAS
SBEAS is a vehicle for customers to access a wide range of Information Technology (IT) Network Centric services and solutions that support the IT lifecycle. It can be used by all other agencies that support an Air Force requirement.
Here is a list of what bidders are required to show mastery of:
- Life-cycle Software Services – Developing/ Implementation, Re-Engineering, Cloud Migration, Modernization, COTS SW and Enterprise Resource Planning [ERP] Systems.
- Cybersecurity – Vulnerability assessments and compliance with IA/Cybersecurity concepts, practices and procedures.
- Information Technology [IT] – Business Analysis, Requirements Analysis, Testing, Validation and Verification, Service /Help Desks, FBAE as a Life-cycle Software service.
- Programming Languages – Java, COBOL, PowerBuilder, .NET, ColdFusion or C, JavaScript, Perl, SQL, PYTHON or PHP Experience, Life-cycle Software Service experience using SWIFT, Ruby On Rails, JavaScript MV Frameworks, or Spark.
- Tools /Development Methodology – Security, Quality, Testing, and Life cycle Methodologies.
- Platforms / Environments – Commercial, non-commercial and/or hybrid cloud, Defense Information Systems Agency [DISA] Enterprise Computing Center [DECC] or Air Force [AF] Computing facilities, DOD and non-DOD, facilities, etc.
- Database Components — Oracle, SQL Server, DB2, SyBase, Postgresql, MarialDB, JasperSoft, or MYSQL; NoSQL database to include: Postgresql, Cassandra, MongoDB, Hadoop, Spark, or CouchDB; RDBMS or NoSQL
- Mobile/Internet of Things (IOT) — Mobile Application Development — Apple iPhone Operating System (IOS), Windows or Android.
- Server Operating Systems — Windows Server, Red Hat enterprise Linux, SUSE, or UBUNTU.
- COTS Product Support
Proposal Requirements/Preparation
According to the draft RFP, potential SBEAS bidders will be required to describe their technical expertise in the aforementioned areas in 20 pages, only. And expertise/experience, not best price, is what evaluators will be expecting.
Due to the fact that there was much consternation about the SBEAS’s NETCENTS II predecessor – it was protested so vigorously immediately after award that it cost years and billions of taxpayer dollars in contract extensions, etc. to clear up – the Air Force is requiring every proposal “t” to be crossed and “i” dotted properly.
Bidders have numerous forms to fill out, including a complex self-scoring work sheet. And the agendas of the Industry Day/Site Visit affairs resembled a lengthy, minutely detailed tutorials on FAR and DFARS. One thing that was stressed particularly strongly was Risk! So, a word to the wise…bidders have to be especially ready and do their homework, be up to snuff on cybersecurity, and address risks convincingly.
WANNACRY – Nine lives? Wanna try?




Leave A Comment